-
 +15 +2
+15 +2Amazon's Ring will sell a $250 security drone that flies around your home
Ring, the Amazon-owned home security business, introduced a flying camera on Thursday that may excite home-surveillance fans but is almost certain to rankle privacy advocates. The $250 drone, called Ring Always Home Cam, is among a slew of products unveiled during Amazon's invitation-only online hardware event.
-
 +26 +1
+26 +1New Windows exploit lets you instantly become admin. Have you patched?
Researchers have developed and published a proof-of-concept exploit for a recently patched Windows vulnerability that can allow access to an organization’s crown jewels—the Active Directory domain controllers that act as an all-powerful gatekeeper for all machines connected to a network.
-
 +30 +3
+30 +3Hacking satellite internet connections is a lot easier than you'd think
Satellite internet may be convenient but it's also easy to intercept
-
 +26 +3
+26 +3Most cyber-security reports only focus on the cool threats
Academics: Only 82 of the 629 commercial cyber-security reports (13%) published in the last decade discuss a threat to civil society, with the rest focusing on cybercrime, nation-state hackers, economic espionage.
-
 +13 +1
+13 +1Enough with the Linux security FUD
Every few weeks, another security story appears saying how insecure Linux is. There's only one problem with most of them: They're fake news. The real problem is incompetent system administrators.
-
 +23 +5
+23 +5Tesla is finally bringing two-factor authentication to its car app
Last year, Tesla chief Elon Musk announced that the automaker will introduce two-factor verification for its app. The company has yet to make it available, but Musk has revealed it’s finally close to happening. In response to a tweet asking about the feature’s status, Musk said Tesla’s “embarrassingly late” two factor authentication is going through final validation right now.
-
 +18 +3
+18 +3Alexa vulnerability is a reminder to delete your voice history
If you haven't been regularly deleting your voice history with Amazon's voice assistant, Alexa, you could have a good reason to start: a recently fixed vulnerability that would've exposed all your conversations with the smart speaker. On Thursday, researchers from cybersecurity firm Check Point released a report detailing security issues they discovered with Amazon's Alexa, which would've allowed a potential hacker to get a person's conversation logs with the smart speaker, as well as install skills on the device without the person knowing.
-
 +19 +3
+19 +3ATM Hackers Have Picked Up Some Clever New Tricks
In the decade since the hacker Barnaby Jack famously made an ATM spit out cash on stage during the 2010 Black Hat security conference in Las Vegas, so-called jackpotting has become a popular criminal pastime, with heists netting tens of millions of dollars around the world. And over time, attackers have become increasingly sophisticated in their methods.
-
 +18 +1
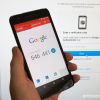
+18 +1It's time to stop using SMS for two-factor authentication
Not all 2FA is equal. Using SMS to get a code might not be "better than nothing" after all.
-
 +21 +8
+21 +8Chinese hackers have pillaged Taiwan’s semiconductor industry
Taiwan has faced existential conflict with China for its entire existence and has been targeted by China's state-sponsored hackers for years. But an investigation by one Taiwanese security firm has revealed just how deeply a single group of Chinese hackers was able to penetrate an industry at the core of the Taiwanese economy, pillaging practically its entire semiconductor industry.
-
 +22 +2
+22 +2An '80s File Format Enabled Stealthy Mac Hacking
The now-patched vulnerability would have let hackers target Microsoft Office using Symbolic Link—a file type that hasn't been in common use in over 30 years.
-
 +21 +4
+21 +4Uniting for better open-source security: The Open Source Security Foundation
We can make open-source software safer and more secure when we all work together.
-
 +20 +2
+20 +2New ‘unpatchable’ exploit allegedly found on Apple’s Secure Enclave chip, here’s what it could mean
One of the major security enhancements Apple has brought to its devices over the years is the Secure Enclave chip, which encrypts and protects all sensitive data stored on the devices.
-
 +19 +3
+19 +3Linux distros fix new Boothole bug
The recently revealed Boothole bug in Grub2, a bootloader used by almost all Linux distributions, has been fixed. But while it's getting headlines, it can only successfully attack a handful of already vulnerable systems.
-
 +17 +3
+17 +3Williams Racing Needs World-Class Performance On The Track And Security
When everything is measured in microseconds, nothing can be allowed to slow the action down, not even the security required to protect the data systems of the legendary William Racing team. "Every week or two the entire racing team locates to another track, and takes their mobile data center with them." And they have to keep it secure. Here's how they do it.
-
 +30 +5
+30 +5Randomness theory could hold key to internet security
Is there an unbreakable code? The question has been central to cryptography for thousands of years, and lies at the heart of efforts to secure private information on the internet. In a new paper, Cornell Tech researchers identified a problem that holds the key to whether all encryption can be broken—as well as a surprising connection to a mathematical concept that aims to define and measure randomness.
-
 +19 +3
+19 +3The next generation of the Purism Linux laptop is on its way
If you want a free software and security first Linux desktop, keep an eye out for Purism's forthcoming Librem 14 laptop.
-
 +19 +4
+19 +4How to Stay Safe from Cyber Attacks?
It is common knowledge that we are constantly at risk from cybercriminals trying to get access to our private data.
-
 +21 +5
+21 +5How Two-Factor Authentication Keeps Your Accounts Safe
If you want to keep your online accounts safe, adding two-factor authentication (2FA) is the single most important step you can take. While no security measure is 100 percent hackproof, 2FA is going to go a long way to locking down access to your important accounts. As the name suggests, 2FA adds another level of authentication to the login process.
-
 +13 +1
+13 +1Best VPN Software to Hide IP Address
In today’s world, Globally, people have adopted the Internet as a part of their life as it makes their daily tasks more manageable than before
Submit a link
Start a discussion




















