-
 +17 +1
+17 +1The rise of ransomware
Ransomware is a troubling trend. Novice criminals with little technical savvy and cheap software can generate big payouts and impact enterprise operations. Here's what you need to know about the changing ransomware landscape.
-
 +22 +1
+22 +1Equifax data breach hits nearly half of US – and isn’t over yet
“Horrendous” hack of Equifax, a US firm responsible for millions of people’s credit ratings, is not the biggest in US history, but the data is the most sensitive
-
 +28 +1
+28 +1Inside an Epic Hotel Room Hacking Spree
A vulnerability in hotel keycard locks was a security disaster—and the opportunity of a lifetime for one burglar.
-
 +28 +1
+28 +1Identity theft at epidemic levels, warns Cifas
Cases total nearly 500 a day with people in their 30s the most targeted group, a watchdog warns.
-
 +26 +1
+26 +1The Guy Who Made Up All Those Password Rules Is Sorry
North Korea tensions, password regrets, Shadow Brokers, and more of the week's top security news.
-
 +23 +1
+23 +1There's a Simple New Way to Find Out if Hackers Already Have Your Password
Passwords suck. They're hard to remember, we all have about a million of them, and they're not supposed to be anything easy or memorable like your cat's name (sorry Furball1).
-
 +18 +1
+18 +1Broadcom chip bug opened 1 billion phones to a Wi-Fi-hopping worm attack
Wi-Fi chips used in iPhones and Android may revive worm attacks of old.
-
 +10 +1
+10 +1A quantum of encryption
With computing power increasing faster than ever before, it's possible to crack previously secure encryption, and with the advent of quantum computing, that possibility gets ever closer. So now you must ask: Is your encryption good enough?
-
 +20 +1
+20 +1Samba puts out new security update to address exploit that fueled WannaCry
Vuln hit "all versions of Samba from 4.0.0 onward using embedded Heimdal Kerberos."
-
 +2 +1
+2 +1How AI can help our cybersecurity crisis
Artificial intelligence has become a key weapon in the fight against cyber crooks, rogue hackers, and aggressive nation states, but it's not a magic fix. Experts weigh in on where AI makes sense in an enterprise security strategy, and what's best left to human judgement.
-
 +2 +1
+2 +1What to look for in hiring your next CISO
CISO is a trendy job title, but turnover is high. Here's how to hire one who'll last.
-
 +21 +1
+21 +1New SMB Worm Uses Seven NSA Hacking Tools. WannaCry Used Just Two
Researchers have detected a new worm that is spreading via SMB, but unlike the worm component of the WannaCry ransomware, this one is using seven NSA tools instead of two.
-
 +17 +1
+17 +1Snowden on ransomware attack: 'It's hard being right in the worst possible way'
Edward Snowden called the continuing "ransomware" scourge "a perfect storm of all the problems everyone has been warning about" at a privacy issues conference Monday. The ransomware Wanna Cry, also known as WanaCrypt0r and WanaDecrypt, boosted its effectiveness by using leaked hacking tools apparently stolen from the National Security Agency, where Snowden was an intelligence contractor before he leaked documents outlining bulk surveillance programs.
-
 +30 +1
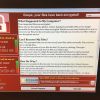
+30 +1'Biggest ransomware outbreak in history' hits nearly 100 countries
A global cyberattack hits international shipper FedEx, disrupts Britain's health system and infects computers in nearly 100 countries.
-
 +12 +1
+12 +1How to secure the network's intelligent edge in the Internet of Things
Much of the IoT's value resides at the network's edge, where organizations collect some of their most sensitive information. Traditional security measures can't always protect this data. Experts weigh in on how to prevent physical access to the network through IoT devices and safeguard the data collected and processed at the edge.
-
 +50 +1
+50 +1WikiLeaks Docs Reveal How The CIA Targets Windows Users
The files mostly pertain to Grasshopper, a framework used to build custom installation executables, and the agency's use of the Carberp malware in its Stolen Goods persistence mechanism.
-
 +1 +1
+1 +1Wikileaks Sets Conditions for Helping Tech Companies Close CIA Hacks
Some companies have been slow to comply.
-
 +2 +1
+2 +1Cybersecurity Workforce Shortage Projected at 1.8 Million by 2022
The results from the eighth Global Information Security Workforce Study (GISWS) have been released this week. The workforce gap is estimated to be growing, with the projected shortage reaching 1.8 million professionals by 2022. While the gap is not news, the fact that it is growing is of great concern to an already exhausted workforce. The question of how to fill the gap has been answered, and millennials are an integral part of the plan. “For years, we’ve known about the impending shortage of the information security workforce, as evidenced by our study year over year,” said David Shearer, CEO,...
-
 +12 +1
+12 +1Government-grade cyber-weapons used against Mexican soda-tax activists
An investigation revealing that Mexican soda tax supporters were targeted with NSO Group's government-exclusive spyware and exploit framework.
-
 +13 +1
+13 +1Viruses, spyware found in 'alarming' number of Android VPN apps
If you've thought of using a VPN to get around the Federal Court’s blocking of The Pirate Bay and other file-sharing websites, you might want to take a closer look.
Submit a link
Start a discussion




















