-
 +14 +1
+14 +1Dell Hell Gets Hotter via Bad Bug in Every PC, Laptop - Security Boulevard
Every Dell endpoint running Windows has a nasty remote-code execution vulnerability. Amazingly, Dell figured it would be great to allow a web page to take full control of a PC—admin privileges and all.
-
 +22 +1
+22 +1Invisible Malware Is Here and Your Security Software Can't Catch It
Sophisticated attackers are now using "invisible malware," a new form of attack that your firewalls can't stop and your anti-malware software can't find nor remove. Here are steps you can take right now to protect your servers and network.
-
 +16 +1
+16 +1Are you using the most-hacked password?
A list of all-too-predictable choices for breached accounts includes 123456 and "Liverpool".
-
 +14 +1
+14 +1How to get developers to do things your way
It is challenging enough for developers to make their code work. But software has to be more than functional. It has to be secure, accessible, and actually reflect what users want. If you need to get developers to provide something beyond the basics, try these motivational techniques.
-
 +33 +1
+33 +1Hacker fakes German minister's fingerprints using photos of her hands
Jan Krissler used high resolution photos, including one from a government press office, to successfully recreate the fingerprints of Germany’s defence minister
-
 +19 +1
+19 +1How a wireless keyboard lets hackers take full control of connected computers
Keystrokes can be recorded, replayed and injected into Fujitsu wireless model.
-
 +16 +1
+16 +15 cybersecurity mistakes companies keep making
A data breach is almost inevitable because we continue to make the same security mistakes. Here are five of the bigs ones, according to experts, and why you simply have to fix them.
-
Analysis+9 +1
The Morris worm at 30
Steven Furnell, University of Plymouth UK, and Eugene H. Spafford, Purdue University USA, turn the clock back 30 years and show that, though bigger, the internet might not be much safer.
-
 +17 +1
+17 +1Fingerprint and face scanners aren’t as secure as we think they are
Current techniques to protect biometric details, such as face recognition or fingerprints, from hacking are effective, but advances in AI are rendering these protections obsolete.
-
 +14 +1
+14 +1Receiving a login code via SMS and email isn't secure. Here's what to use instead
Do you receive a code via SMS message, email or voice call to sign into your bank account? This security method is no longer considered very secure.
-
 +42 +1
+42 +1New flaws in 4G, 5G allow attackers to intercept calls and track phone locations
A group of academics have found three new security flaws in 4G and 5G, which they say can be used to intercept phone calls and track the locations of cell phone users. The findings are said to be the first time vulnerabilities have affected both 4G and the incoming 5G standard.
-
 +21 +1
+21 +1This is bad: the UAE's favorite sleazeball cybermercenaries have applied for permission to break Mozilla's web encryption
Darkmatter is also one of the least-discriminating cybermercenary bands in the world, available to help torturers, murderers and thugs hang onto power by attacking opposition movements and letting the secret police know who to arrest, torture and kill
-
 +21 +1
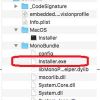
+21 +1Hackers keep trying to get malicious Windows file onto MacOS
Clever trick may be designed to bypass Gatekeeper protections built into macOS.
-
 +25 +1
+25 +1Girl Scouts join global push to 'plant a seed' for women in tech
A new cybersecurity program teaches girls online safety, while giving them tech confidence.
-
 +18 +1
+18 +1How to set up SELinux right, the first time
When you need to run Linux in an especially secure environment, SELinux is the answer. But it takes some know-how to get the hypersecure Linux version up and running.
-
 +7 +1
+7 +1Technology standards: Understanding Transport Layer Security
Need an overview to bring you up to speed? Start with this: TLS is the critical Internet infrastructure that makes commerce, trust, and confidentiality possible.
-
 +41 +1
+41 +1Uncovering What Your Phone Knows
Jennifer Valentino-DeVries, an investigative reporter for The Times, explains how reporters discovered some of the information mobile apps collect.
-
 +20 +1
+20 +1Massive botnet chews through 20,000 WordPress sites
Attackers have infected 20,000 WordPress sites by brute-forcing administrator usernames and passwords.
-
 +16 +1
+16 +1What skills does a cybersecurity professional need?
Cybersecurity professionals are often portrayed as lone hackers in hoodies. But as well as technical skills, they also need to be excellent communicators and have a high degree of personal integrity.
-
Current Event+17 +1
BlackBerry to Acquire Cylance for $1.4 Billion in Cash | SecurityWeek.Com
BlackBerry has agreed to acquire next-generation endpoint security firm Cylance for US $1.4 billion in cash, and the assumption of unvested Cylance employee incentive awards.
Submit a link
Start a discussion




















